Findings
- We present eight attacks that exploit the security and privacy implications of phone number recycling, a regulated industry practice to maintain the availability of ten-digit phone numbers.
- Of those, we empirically evaluated three low-cost reverse lookup attacks on previous owners by analyzing sets of available phone numbers at two U.S. mobile carriers. By analyzing the structure of phone number blocks, we developed an effective strategy for the adversary to discern recycled numbers from fresh ones.
- Most of the available phone numbers we sampled (215 of 259) were recycled and also vulnerable to at least one of the three attacks—PII indexing, account hijackings via recovery, and account hijackings without password reset.
- At one carrier, we estimated the number of available recycled numbers to be about one million, with a largely fresh set of numbers becoming available each month.
- We found that the online number change interfaces at both carriers imposed few restrictions on the adversary's ability to browse and obtain vulnerable recycled numbers.
- Neither carrier publicly documented their number recycling policies. Worse, they provided inconsistent responses when we asked on 26 occasions. Subscriber confusion could be a faciliting factor in the prevalence of number recycling attacks. After reviewing our disclosure and recommendations, the two carriers in our study have made changes to better inform their subscribers about phone number recycling.
- We obtained 200 recycled numbers for one week, and found 19 of them were still receiving security/privacy-senstive calls and messages (e.g., authentication passcodes, prescription refill reminders). New owners who are unknowingly assigned a recycled number may realize the incentives to exploit upon receiving unsolicited sensitive communication, and become opportunistic adversaries.
Reverse lookup attacks
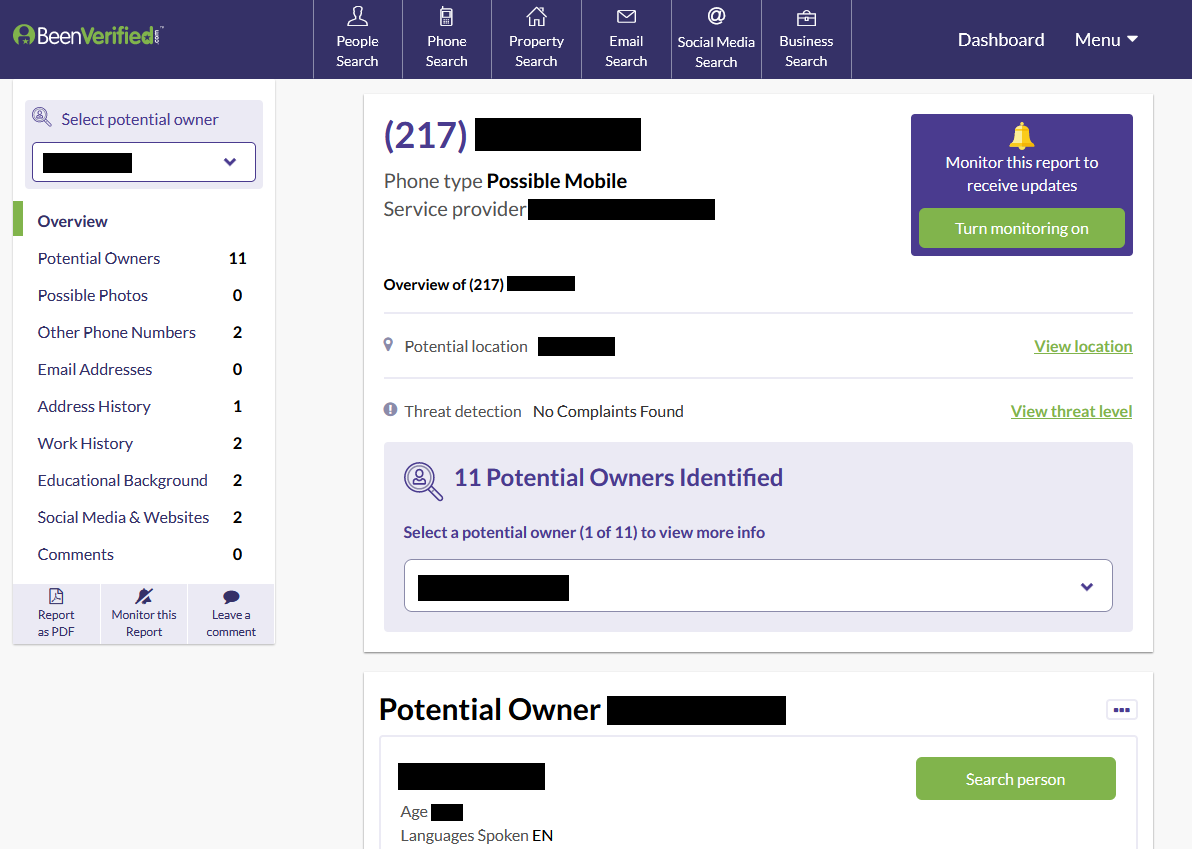
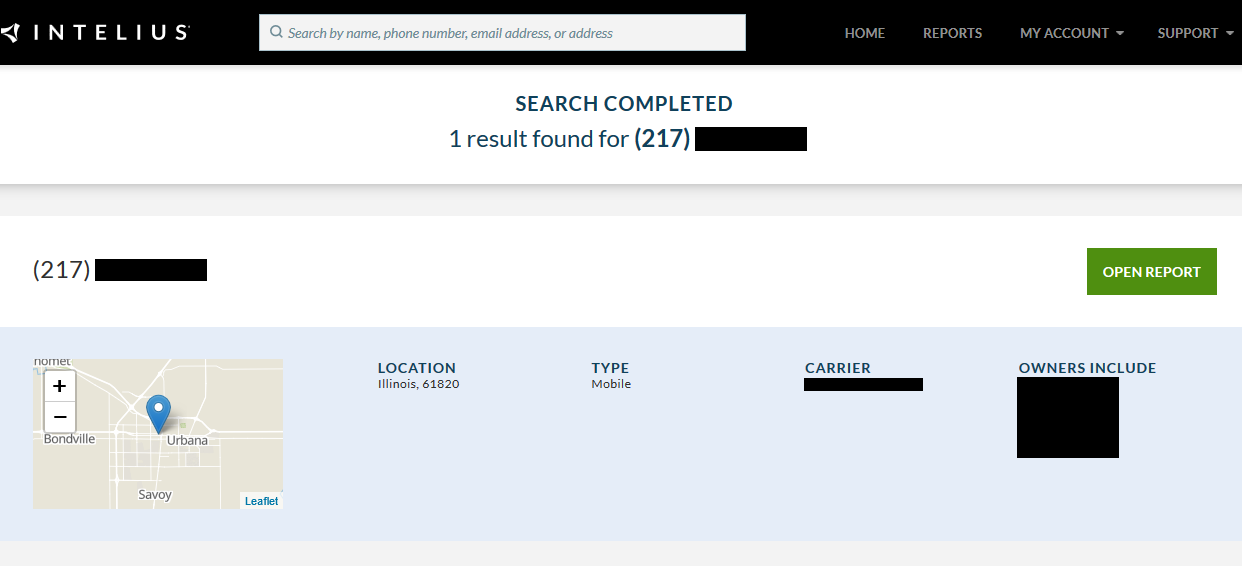
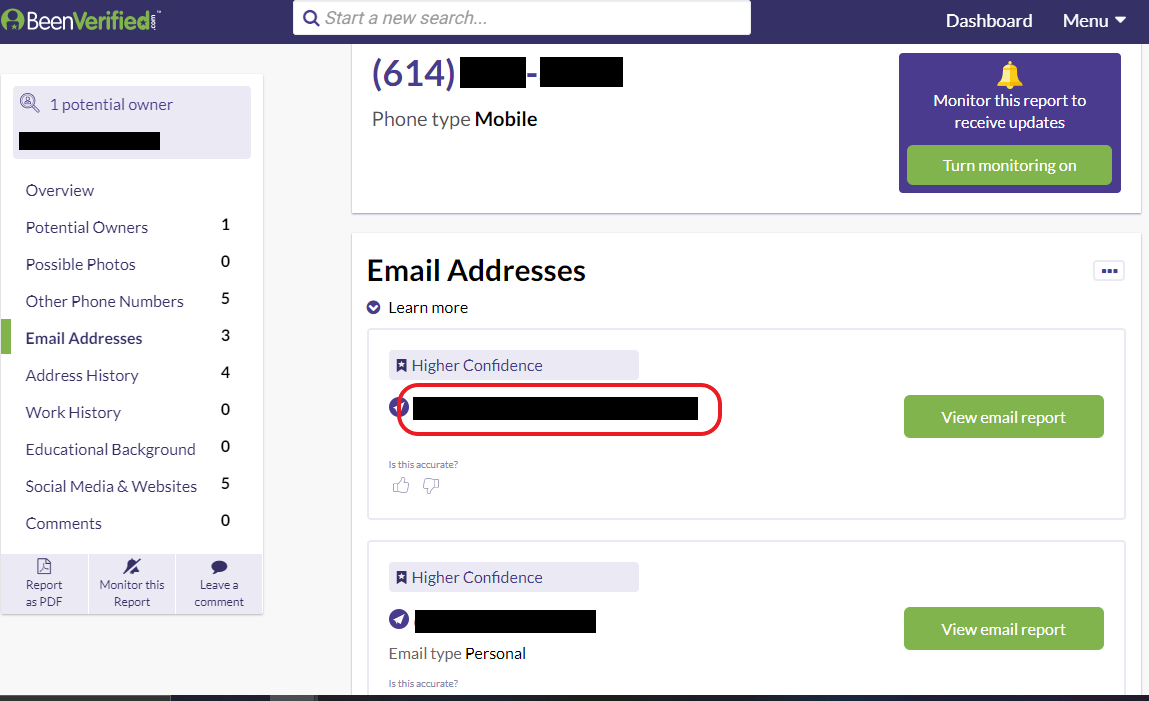
171 of the 259 available numbers we sampled led to hits on people search services, which provide personally identifiable information (PII) on previous owners.
The adversary can leverage people search services—which aggregate information on the web about individuals—to gather PII on previous owners and associates. Once they obtain the previous owner's number, they can perform impersonation attacks to commit fraud or amass even more PII on previous owners.
For the 259 numbers we analyzed, 171 produced a hit at either BeenVerified or Intelius.
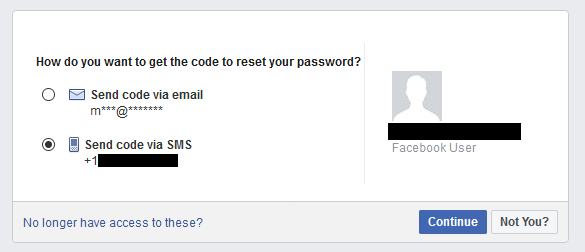
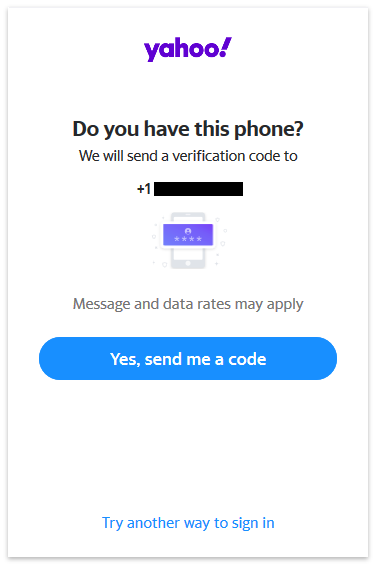
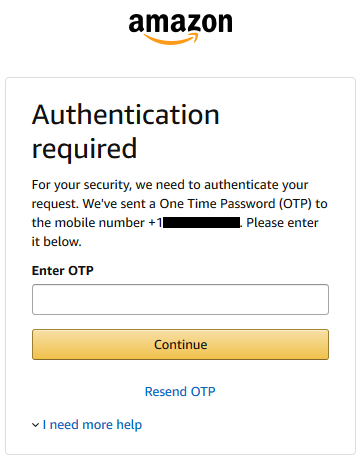
171 of 259 numbers we sampled were vulnerable to account hijackings at six popular websites: Amazon, AOL, Facebook, Google, Paypal, and Yahoo.
An attacker can cycle through the available numbers shown on online number change interfaces and check if any of them are associated with online accounts of previous owners. If so, the attacker can then obtain these numbers and reset the password on the accounts, and receive and correctly enter the OTP sent via SMS upon login.
Of the 259 numbers in our sample, 171 had a linked account on at least one of the six websites.
100 of the 259 numbers were linked to leaked login credentials on the web, which could enable account hijackings that defeat SMS multi-factor authentication.
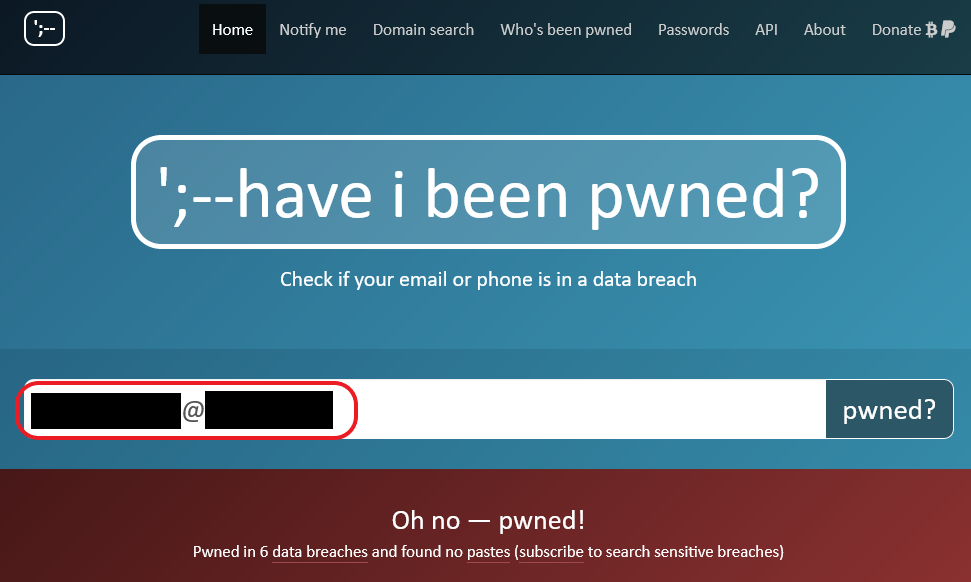
An attacker can use people search services to look up previous owners' email address(es), then check if the email addresses have been involved in data breaches. If the breaches involve passwords, the attacker can obtain the password on cybercriminal marketplaces and break into SMS 2FA-enabled accounts without having to reset the password. For the email addresses found on people search services, we checked for involved data breaches on Have I Been Pwned? (HIBP)—an online service that allows users to check whether their credentials and other identifying information have been compromised in data breaches.
In total, we found 100 phone numbers with associated email addresses that had been involved in a password breach and had linked profiles on at least one of the six websites.
More number recycling threats
Along with the three low-cost reverse lookup attacks, we present five additional number recycling exploits that can target both previous and future owners.
| Attack | Threat(s) | Population(s) affected |
|---|---|---|
| Targeted takeover. Attacker learns that an acquaintance's contact has changed (e.g., stalker calls and gets a cancelled number intercept message, friend changes their number and tells everyone). They keep track of the aging period, and obtain the number once it becomes available. | Hijack online accounts; impersonate/stalk previous owner; read new messages intended forthe previous owner | Previous owners, especially intimate partner violence (IPV) survivors changing their numbers to escape abusers |
| Phishing. Attacker logs available numbers but does not obtain them. Later, they keep checking whether the numbers are still available. Once a number is assigned to a new subscriber, they can phish the subscriber through SMS (e.g., "Welcome to your new service. Click here to enable high-speed data for your account"). Subscribers are more likely to fall for phishing attacks when the message sounds believable. | Hijack victims' online phone account; potentially hijack victim's phone number | Subscribers who have been assigned a new number, whether fresh or recycled |
| Persuasive takeover. Attacker logs available numbers but does not obtain them. After the number is assigned, they can spoof a carrier message (e.g., "Your number is part of an ongoing investigation on the previous owner and needs to be reclaimed. Please change your number online") and obtain the number for himself after the aging period. | Hijack linked online accounts; impersonate victim; read new messages intended for the victim | Subscribers who have been assigned a new number, whether fresh or recycled |
| Spam. Attacker obtains a number, intentionally sign up for various alerts, newsletters, campaigns, and robocalls, and then release the number for recycling | Victim harassed with unwanted texts and calls; account calling balance depleted | Subscribers who have been assigned a recycled number |
| Denial of service. Attacker obtains a number, signs up for an online service that requires a phone number, and releases the number. When a victim obtains the number and tries to sign up for the same service, they will be denied due to an existing account. The attacker can contact the victim through SMS and demand payment to free up the number on the platform. | Denial of service; victim needs to pay ransom to use platform | Subscribers who have been assigned a recycled number and are new users of online services that require a unique phone number |
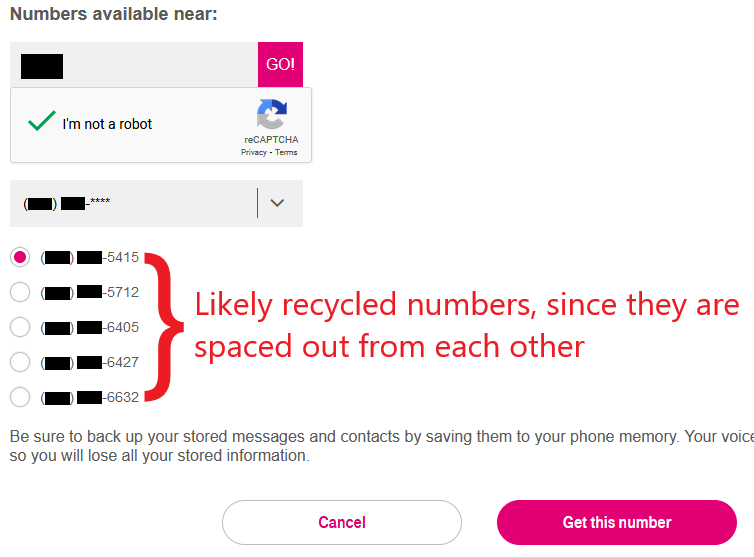
Recycled numbers are easy to spot
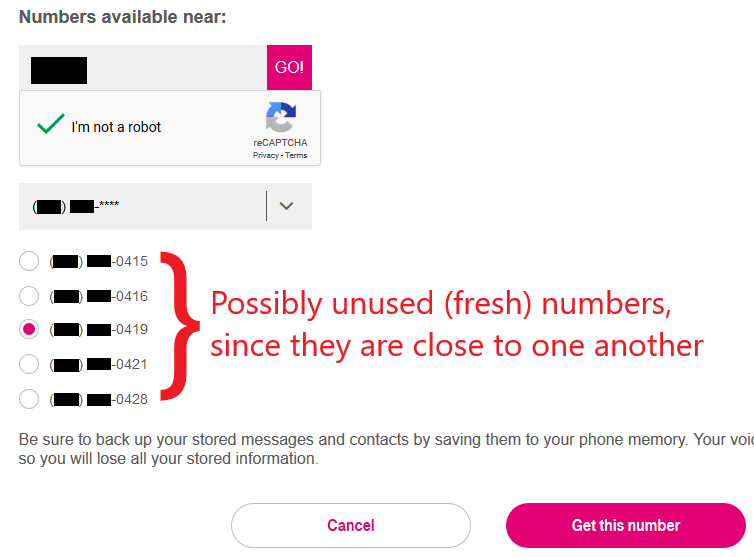
At both carriers, available numbers are fully visible and grouped by NPA-NXX (their first six digits, which are usually unique to each carrier). We developed a strategy to focus on recycled numbers: if no two available numbers are within 10 of each other, then all the numbers in the NPA-NXX are likely recycled. Otherwise, the NPA-NXX is possibly fresh, and its numbers possibly unused (never previously assigned). The adversary can use this strategy to focus their attention on NPA-NXX blocks that contain primarily recycled numbers, while ignoring blocks that contain primarily fresh numbers.
We used the reverse phone lookup tools at BeenVerified and Intelius to validate our strategy. We did so by randomly sampling 159 and 100 numbers from Verizon's and T-Mobile's possibly unused groups respectively and looking for people search hits. We found that 53/159 and 44/100 of the sampled possibly unused numbers returned hits, compared to 96/159 and 75/100 of the sampled likely recycled numbers.
Responses
- In December 2020, T-Mobile informed us that after reviewing our research, it had updated its number change support page to 1) remind subscribers to update their contact number on bank accounts and social media profiles, and 2) specify the FCC-mandated number aging period.
- Along with raising subscriber awareness, it also informed us that customer service agent manuals had been updated to emphasize those two points during relevant interactions, effective early December.
- In December 2020, CTIA—the U.S. trade association representing the wireless communications industry—informed us that after reviewing our research, Verizon had updated its public-facing support document for number cancellations, suspensions, and transfers to 1) remind subscribers to update their contacts and unlink their business and online accounts, and 2) specify the FCC-mandated minimum aging period (45 days).
Revisions
Update (January 27, 2022): We have released the peer-reviewed post-print, which will be contentwise identical to the publisher version. The original pre-print can be found here.
Citation
@inproceedings{lee2021security,
author={Lee, Kevin and Narayanan, Arvind},
title={{Security and Privacy Risks of Number Recycling at Mobile Carriers in the United States}},
booktitle={{Proceedings of the 2021 APWG Symposium on Electronic Crime Research (eCrime)}},
year={2021},
pages={1--17},
publisher={{Institute of Electrical and Electronics Engineers (IEEE)}},
isbn={978-1-6654-8029-1},
issn={2159-1245},
doi={10.1109/eCrime54498.2021.9738792},
}